
The website for ODIN Intelligence, a company that provides technology and tools for law enforcement and police departments, was defaced on Sunday.
The apparent hack comes days after Wired reported that an app developed by the company, SweepWizard, which allows police to manage and coordinate multi-agency raids, had a significant security vulnerability that exposed personal information of police suspects and sensitive details of upcoming police operations to the open web.
ODIN provides apps, like SweepWizard and other technologies, to law enforcement departments. It also provides a service called SONAR, or the Sex Offender Notification and Registration system, used by state and local law enforcement to remotely manage registered sex offenders. But the company has also been the subject of controversy. Last year, ODIN was found to be marketing its facial recognition technology for identifying homeless people and describing those capabilities in callous and degrading terms.
It’s not clear who defaced ODIN’s website or how the intruders broke in, but a message left behind quoted ODIN founder and chief executive Erik McCauley, who largely dismissed Wired’s recent reporting that found the SweepWizard app was insecure and spilling data.
“And so, we decided to hack them,” the message left on ODIN’s website said.
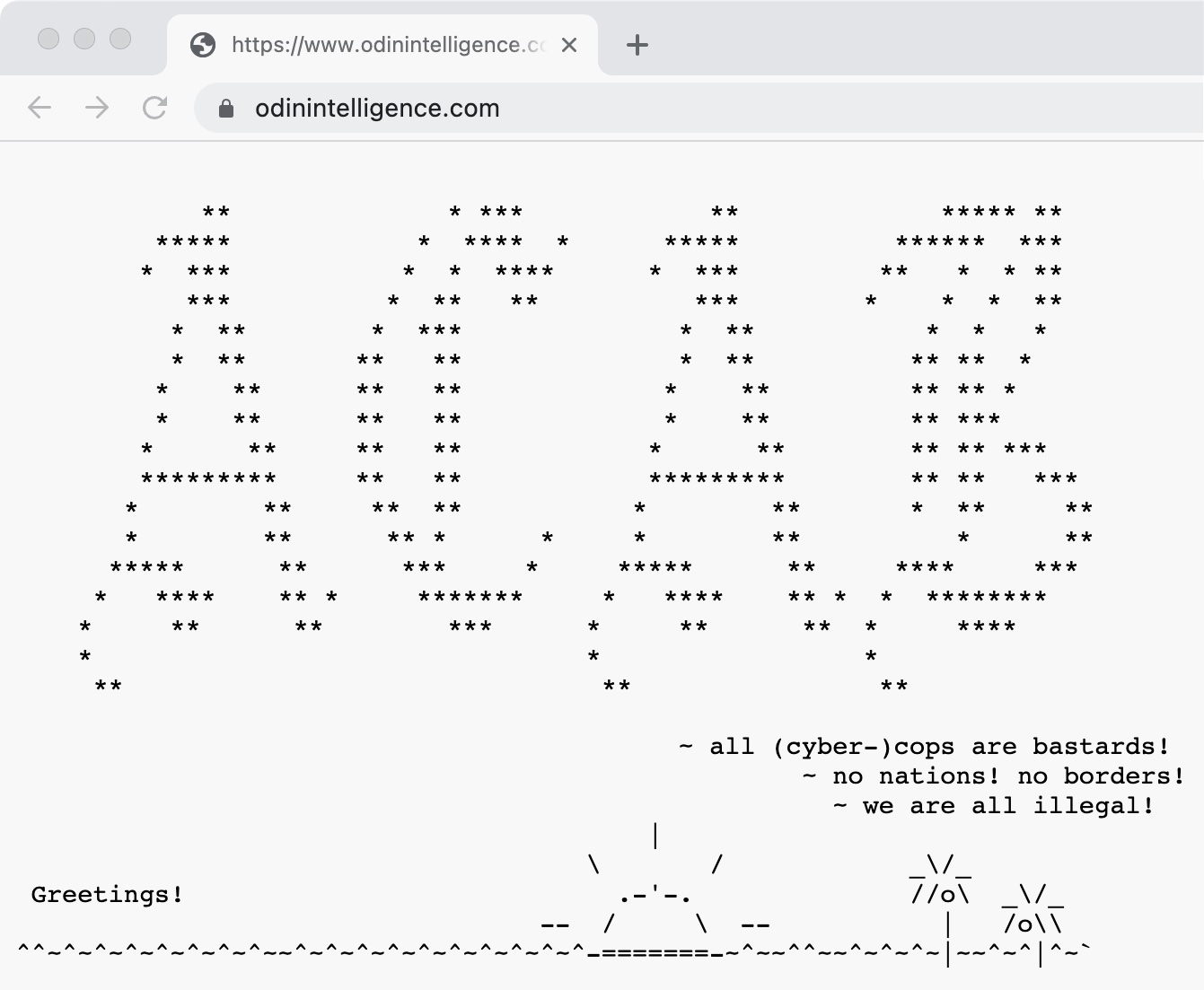
A defacement message on ODIN Intelligence’s website spelling ACAB, an acronym for “All Cops Are Bastards.” Image Credits: TechCrunch (screenshot)
The text of the defacement is ambiguous as to whether the hackers exfiltrated data from ODIN’s systems or if, as it claims, “all data and backups have been shredded,” suggesting that there may have been an attempt to erase the company’s stores of data.
Emma Best, co-founder of non-profit transparency collective DDoSecrets, told TechCrunch that data was exfiltrated from ODIN’s servers and that the organization was in possession of it. “We received the data the other day and are processing it,” Best said.
The defacement note made note of three large archive files, totaling more than 16 gigabytes of data, each named in relation to ODIN’s organization, the sex offenders’ data, and the SweepWizard app. The hackers also left hashes, a unique string of letters and numbers that serve as a signature for each file. Best confirmed that the files that DDoSecrets received matched the hashes in the defacement post.
The defacement also included a set of Amazon Web Services keys, apparently belonging to ODIN. TechCrunch could not immediately confirm that the keys belong to ODIN, but the keys apparently correspond with an instance on AWS’ GovCloud, which houses more sensitive police and law enforcement data.
ODIN chief executive Erik McCauley did not return emails from TechCrunch with questions about the defacement and apparent breach, but ODIN’s defaced website was pulled offline a short time later.
In a financial filing on Thursday, T-Mobile revealed that a hacker accessed a trove of personal data belonging to 37 million customers. The telecom giant said that the “bad actor” started stealing the data, which includes “name, billing address, email, phone number, date of birth, T-Mobile account number and information such as the number of […]
SC Media UK has collected predictions across a range of categories from cybersecurity experts. Here we give you the roundup… What might 2023 bring in term of cyber? Our experts found consensus on a few areas. First, boardroom metrics will become more important as senior execs demand transparency through quantified insights on the company’s security posture. […]
In 2019, Ring launched the Peephole Cam, a camera that fits over existing door peepholes to record goings-on outdoors, in apartment building hallways and so on. Priced at $199, the Peephole Cam failed to catch on, leading Ring to discontinue it in 2021. But now, Ring’s giving it another go — the Peephole Cam made […]
Leave a Reply