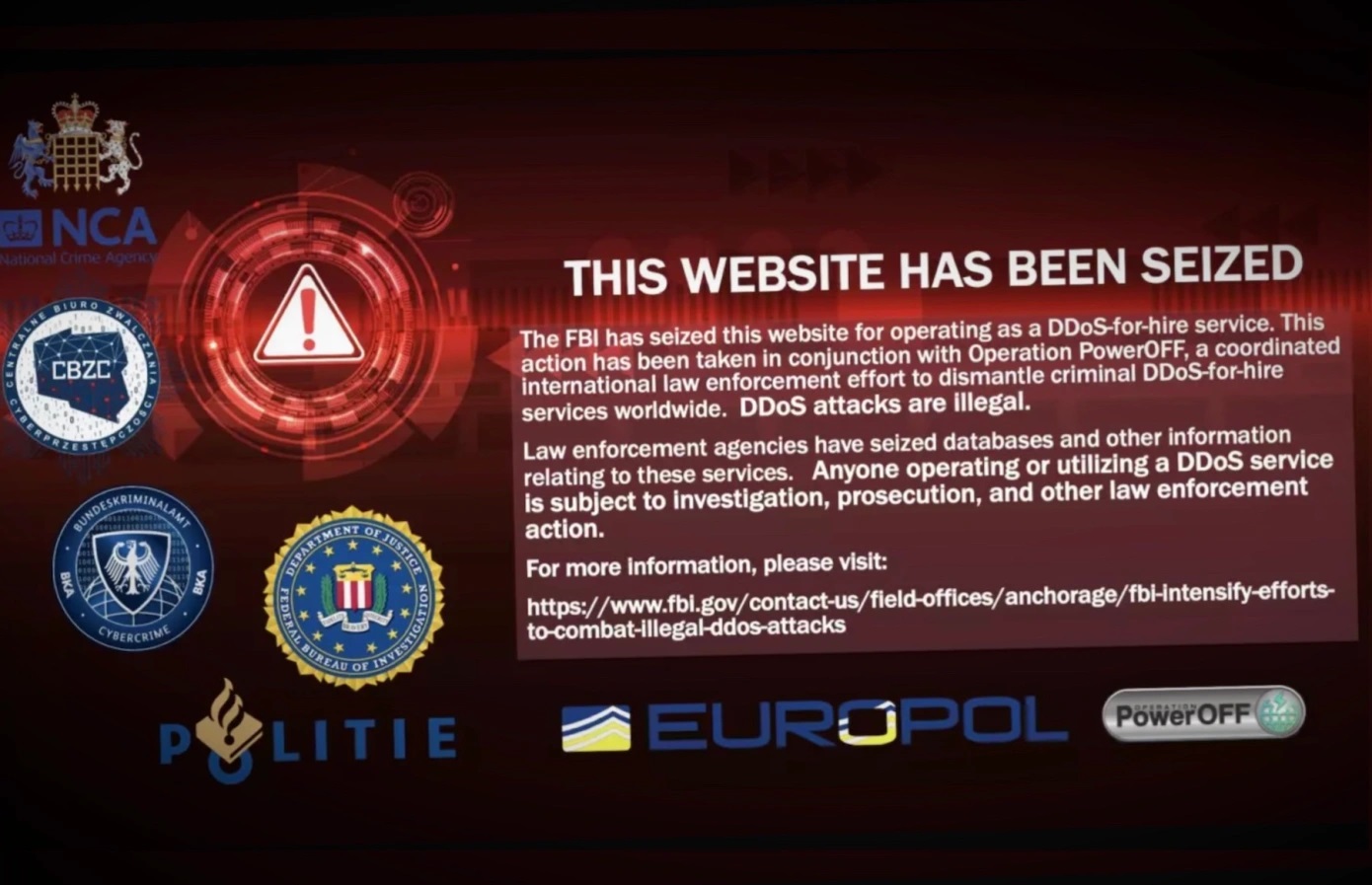
U.S. officials say they have seized dozens of domains linked to some of the world’s leading distributed-denial-of-service-for-hire websites. But TechCrunch found that several of the seized sites are still online.
In a press release on Wednesday, the U.S. Department of Justice announced the takedown of 48 domains associated with some of the world’s most popular DDoS booter platforms, according to the corresponding warrant. These services, often marketed as sites for bandwidth stress-testing networks, allow low-skilled individuals to carry out DDoS attacks designed to overwhelm websites and networks and force them offline.
The takedowns were carried out as part of a joint operation between the U.K.’s National Crime Agency, Dutch police and Europol, known as “Operation PowerOFF.”
The DOJ said these booter sites were involved in attacks against a wide array of victims in the U.S. and abroad, including educational institutions, government agencies and gaming platforms. Europol notes that one of the sites seized has been used to carry out more than 30 million attacks.
While many of the websites targeted by the operation now display a message stating they have been seized by the FBI, TechCrunch found that — at the time of writing — at least eight of the sites supposedly seized by U.S. prosecutors continue to load as normal. It’s unclear why these sites continue to load.
Operation PowerOff also saw law enforcement officials arrest seven individuals who allegedly oversaw the DDoS booter services. In the U.S., criminal charges have been filed against six individuals: John M. Dobbs, Jeremiah Sam Evans, Angel Manuel Colon Jr., Shamar Shattock, Cory Anthony Palmer and Joshua Laing.
At the time of writing, the DDoS-for-hire service allegedly run by Laing remains online.
DOJ spokesperson Thom Mrozek told TechCrunch that there was a delay in getting the FBI splash-pages. “We are working with the registries to make this happen.” Mrozek said while some sites remain online, the sites are “no longer functioning” and cannot be used to launch attacks.
The U.K.’s NCA announced that it has also arrested an 18-year-old man in Devon, who is suspected of being an administrator of one of the seized sites. The NCA added that customer data from all of the DDoS booter sites was obtained and will be analyzed by law enforcement.
“Admins and users based in the UK will be visited by the National Crime Agency or police in the coming months,” the NCA warned.
sourse: https://techcrunch.com/
With lidar companies Ouster and Velodyne officially merged, CEO Angus Pacala has identified the next phase of growth. And it’s not self-driving cars or even advanced driver assistance systems. It’s smart infrastructure. “I keep saying this and people think I’m crazy, but there’s a good chance that smart infrastructure becomes our biggest vertical by a long shot […]
Welcome back to This Week in Apps, the weekly TechCrunch series that recaps the latest in mobile OS news, mobile applications and the overall app economy. The app economy in 2023 hit a few snags, as consumer spending last year dropped for the first time by 2% to $167 billion, according to data.ai’s “State of Mobile” report. However, […]
government watchdog has published a scathing rebuke of the Department of the Interior’s cybersecurity posture, finding it was able to crack thousands of employee user accounts because the department’s security policies allow easily guessable passwords like ‘Password1234’. The report by the Office of the Inspector General for the Department of the Interior, tasked with oversight […]
Leave a Reply